It seemed like a legitimate email. At least until the dreaded pop-up appeared telling you that your files had been encrypted. Ok, take a deep breath, you have an anti-virus program to get rid of malware. But this is different. This is asking for money to get your files back. And there’s a time limit? It’s like something out of a hostage movie. And unless you’ve been backing up your files – or are secretly Liam Neeson in Taken – you may have to pay the ransom. Wait, there’s another option? That’s right, you can also choose to infect two of your friends with this software in exchange for a free key to decrypt your files. To pay or to infect? That is the question.
Ladies and gentlemen, welcome to the new era of ransomware.
A Modern-Day Sophie’s Choice
Ransomware attacks are skyrocketing as cybercriminals continue to find new ways to infect individual and corporate computers in an effort to get their piece of this $1 billion dollar industry. While most ransomware has a pay-to-retrieve format – like last month’s WannaCry, the biggest cyber-attack in history, infecting more than 230,000 computers in four days – there’s a new variation on the scene. It’s called Popcorn Time and it’s the ultimate test of your moral compass – pitting you against your friends, family or coworkers as you decide whose data is more valuable. Sophie, eat your heart out.
It’s like there is an industrial cybercriminal kitchen that continuously churns out new recipes with new ingredients and we are the taste testers. If the software can be improved – in other words, it’s easy to bypass the ransomware – these cyberchefs head back to their pantry and search for that secret something that will perfect the dish. Think of ransomware as movie theater popcorn with layers of butter and Popcorn Time like it’s artisanal truffle butter big brother – both delicious, but one has that extra something. Unfortunately, in this case, ransomware attackers aren’t testing our flavor preferences, but rather our morality and pocketbooks. And they still haven’t found the perfect combination of ingredients, so it is likely we will be seeing new menu items in the near feature.
What is ransomware?
Ransomware is malicious software that either disables access to a target device (locker ransomware) or encrypts files (crypto ransomware) with the intent of holding them hostage until the user agrees to pay a specified ransom to regain access. While the first iteration appeared as far back as 1989, ransomware began garnering public attention with the Trojan.GPcoder in 2005. This multi-layer malware has quickly evolved into one of the most popular methods for cybercriminals to hijack your computer – and make some quick cash.
How does ransomware work?
While there are many ways for ransomware to infect computers, the most common is through email. Hackers send phishing campaigns – infected messages – that when opened will download the malware to a device. Sometimes these emails are obvious (Did you really think a Nigerian prince would ask you for money?), while some are disguised as invoices or pay slips and others are sent directly from a hacked account from your contacts list.
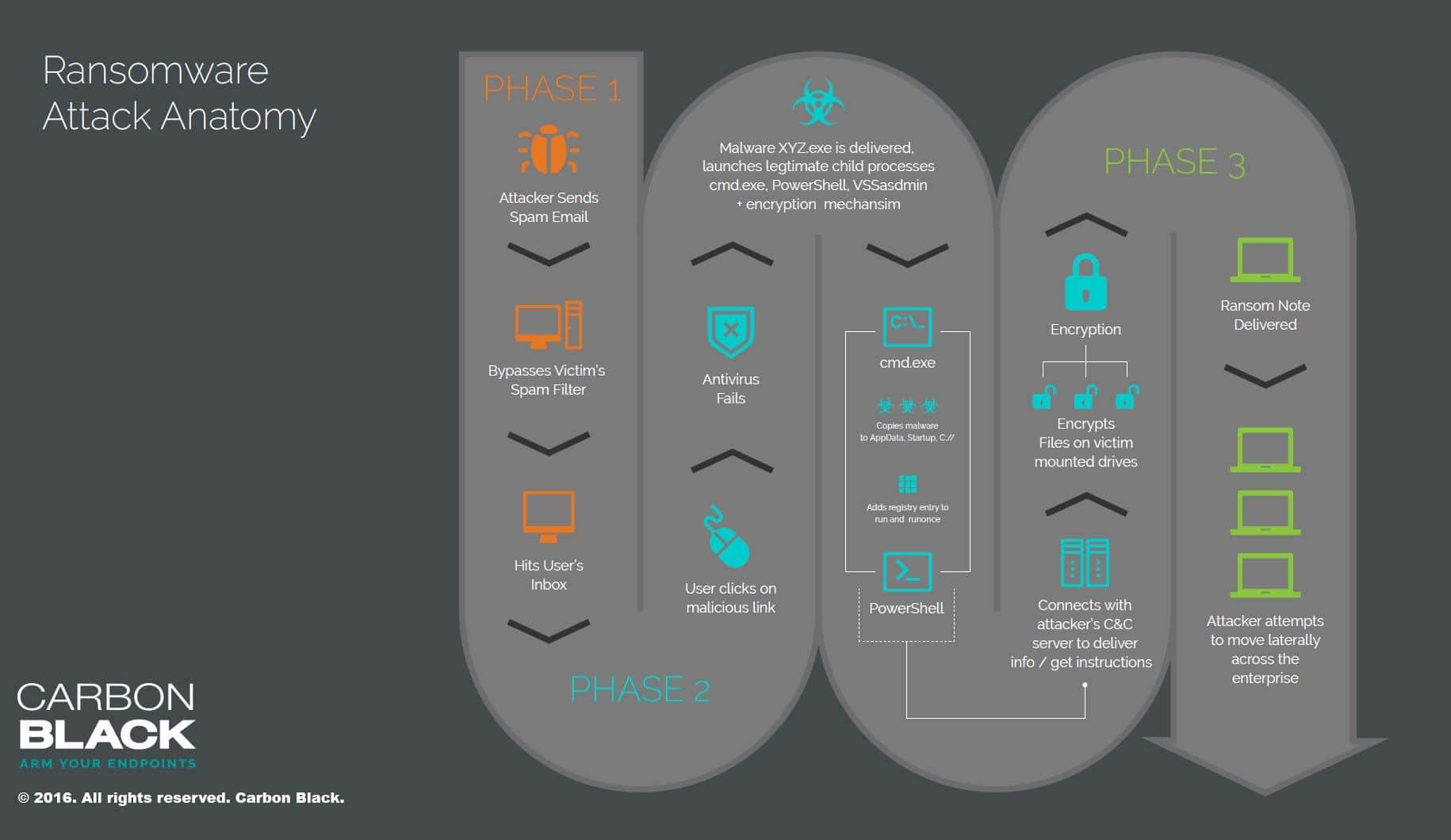
Other means for spreading ransomware include infected USBs, downloading files from untrusted websites and malvertisements (infected online advertisements).
How common are ransomware attacks?
According to Symantec, global ransomware attacks rose 36% in the last year with “100 new malware families released into the wild.” Kaspersky further supports these findings showing businesses went from being attacked once every 2 minutes to once every 40 seconds. And as the number of affected companies and individuals grows, so does the ransom. Last year, you could expect to pay an average of $1,077 to get your data back (up from $294 in 2015), while only time will tell how much that rate will continue to rise.
Do I have to pay?
Technically, no you don’t have to pay – and cybercrime authorities discourage giving in to this extortion. However, each case depends on the individual or company involved and it’s important to assess the situation before making any decisions. Consider the following:
- How much data was compromised? Some attacks only affect one computer, while others creep into the entire network. Evaluate what exactly was infected and whether you can continue operations without this information.
- Did you back up your server? We can’t stress enough how important it is to regularly back up your data, especially with ransomware on the rise. With your files protected on a separate hard drive, cloud or server, you will be able to start from where you left off without having to pay.
- How long will it take to return to normal operations? 72% of employees with infected computers were locked out of their files for two days, while 17% were blocked for ten. This could cripple the productivity and operations of businesses running on a smaller scale, while others – like hospitals – simply can’t afford to have prolonged down periods due to the nature of their work.
Only 34% of people worldwide do not pay when they encounter ransomware. And while this number is higher in the US (64%), it’s important to recognize that payment is not required. Weigh your options carefully and determine what will work best for your specific case. Also, keep in mind that you are dealing with criminals, so there is no guarantee they will follow through after you pay. In fact, 20% of those who paid the ransom did not receive their decryption key.
How can I prevent ransomware?
The best way to avoid ransomware is to keep it from infecting your computer in the first place. It may seem like common sense, but as hackers continue to innovate, it’s up to individuals and companies to be proactive and implement precautionary measures:
- Back up your system. Always, always, always back up your files on an external system. If you have a great deal of important data, consider setting up two backups: an external hard drive and a cloud-based system. Note: if you only have a physical hard drive as a backup, be sure to disconnect it from the network when back up is completed to prevent it from attacks.
- Install monitoring software. Computer monitoring software, like FlexiSPY, gives you an added layer of protection. Know immediately if anyone is visiting risky websites, downloading pirated files or using external storage devices that could compromise the security of your network.
- Use a strong anti-virus. Regularly update your anti-virus program and consider paying for a more powerful version, especially if you need to protect important company information.
- Be aware. Educate yourself on the dangers and signs of ransomware. Taking time to know what to look for and how to avoid it will decrease your likelihood of being attacked – and hopefully save you some money and stress. When in doubt, don’t click about!
What if I do get infected?
If you do find yourself hit by WannaCry, Popcorn Time or another variation of ransomware, there are steps to take for rectifying the situation:
- Disconnect the infected computer. Taking your machine offline will keep it from spreading any malware to other machines on the network.
- Download ransomware removal tools. See which software would work best for your case, but keep in mind that with so many types of malware, no product is 100% guaranteed.
- Visit www.nomoreransom.org. This international initiative is made up of some of the world’s leading cybersecurity and cybercrime players who “have joined forces to disrupt cybercriminal businesses with ransomware connections.” They have a number of decryption keys available that may be the answer to regaining control of your computer.
