“You’ve probably heard about the celebrity pictures that were stolen and linked all over over the internet.. Furthermore you probably also know that Apple’s iCloud was -at least in part- at fault”
But what you may not be aware of is just how easy the whole thing was, and how, using applications that are simple to find, you too can gain access to practically anyone’s iCloud account – and you don’t need to be a hacker to do it.
Notice: Everything in this article is for educational purposes only. Apple most likely have fixed the exploits that lead to the data leak so this is just a proof of concept article showing how it was most likely done. FlexiSPY is not responsible for any damages, loss or anything else that incurs if you do try to recreate these steps.

How Did The Leak Happen?
According to reports it was simply due to the accounts that were compromised being unsecure. For example they failed to turn on two-step notification for their account or their password was just too easy to guess. Once access was gained in to the accounts, and because most iPhone users happily let their device upload all pictures to their iCloud account without ever thinking of the consequences, a second piece of software was used to then download all backups of said iPhone.
Once those backups were downloaded the same program was used to explore its contents and this includes the pictures and videos that are now all over the internet and are being investigated by the FBI
So who is to blame? Apple for not making it clear enough that iCloud backs up everything? Apple for not making sure two-step sign up is mandatory? The user for not really fully understanding the implications of having their data stored in the cloud which can potentially be hacked?
If you own an iPhone every picture you take is uploaded to your iCloud account once you have signed in to the iPhone using your Apple ID. However this can be easily turned off (we stress that Apple have fixed the exploits so that passwords cannot be guessed by brute force which makes this hack no longer possible) so that you are no longer vulnerable.
The process that led to the leak consists of several steps.
2 Ways It Might Have Been Pulled Off
- First off, the hackers needed to have access or know the email address of the persons targeted.
- They used those email addresses to login to iCloud and guess the security password
- They gained access to the account and then proceeded to download any iCloud backups.
Or it could have been done this way:
- The hackers knew the email addresses of the people they wanted to target.
- Hackers used a brute force tool and password list to guess the passwords.3. They gained access to the acocunt and then proceeded to download the iCloud backups.
Either way, one thing that hasn’t come to the surface yet is how the hackers got the email addresses to start with.
However there are many darknets where information like this is traded via the use of the encrypted TOR browser.
Replicating The Hack
This is done entirely for educational processes and, from the latest information, Apple have already fixed the iCloud vulnerabilities. So, for this we will just show you, hypothetically how it was done but we will investigate the software used to download and extract iCloud backups in more detail.
The first thing is to obviously know the email address of the people you wish to target. We are using our own Apple ID that we have set up which already contains an iCloud backup. However the program that is being pointed at to guess the passwords was called iBrute.

So, for this, we are going to assume that we already have an account (Apple ID) whose password we know (which we do) so, because Apple fixed the exploit the next step is written from the perspective that iBrute worked and gave us an email address and password.
Before we proceed to the next section we need to understand just how iCloud works on an iPhone after you enter your Apple ID which is like this.
- Enter your Apple ID on the iPhone – iCloud is enabled by default which photo sharing enabled.
- Set up a new photo stream on the iPhone and add pictures – wait for them to be uploaded to iCloud
- For PC download and install the iCloud Control Panel
- Once it is installed you are asked to log in to iCloud.
- You then click the Options button under Photos to see the photos that were be uploaded to iCloud
- You can set the options to upload all photo streams from the iPhone to iCloud.
- You can then see the iCloud photos that are stored on your PC.
What you may not be aware of is that even though photo sharing is enabled by default it is not as easy as logging in to any iCloud account and viewing the pictures online. iCloud does not work that way and even though we have set up a photo stream as a test it will not appear on the iCloud website.
Below you can see the photo stream on our PC we are using. We have added 3 extra pictures (you can just drag and drop any image file into the iCloud photos folder and it will sync.
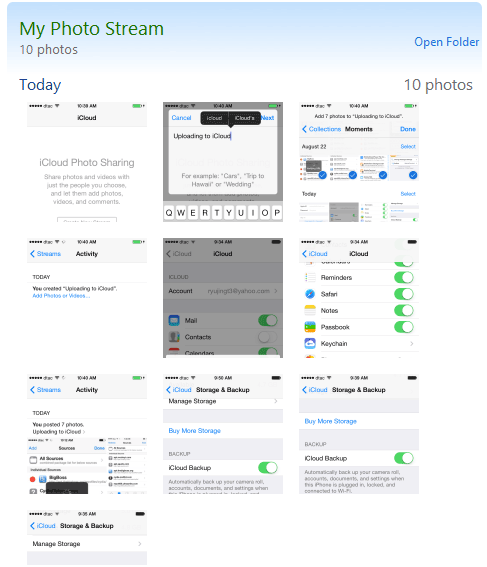
So how does iCloud actually work?
- Sign into iCloud on any iDevice using your Apple ID
- Set up photo streaming and photo sharing in iCloud
- Take some pictures or videos on the device
- Login to a new iDevice with the same account.
- All pictures and videos taken will appear on the new device.
So essentially iCloud is the backend that hosts and shares all pictures and vides (and other content such as emails and contacts) between all iDevices your account is logged in to but this also means that picture and videos backed up to iCloud are only visible on the specific iDevice.
So how do you get access to the pictures or videos if you cannot do it directly from iCloud itself?
This is the next thing we will discuss and where things get clever.
Backing Up To iCloud
Apple makes it pretty damn easy to back up data to the cloud, in-fact, it’s enabled on a persons iOS device by default. This includes automatic backup of photos from the camera roll.
All you need to be back up the phone is to make sure that your phone is charging, connected to wifi, and is locked. Once the device is backed (specifically iCloud) you’re able to perform the same steps that the hackers used to get access to the information.
Apple, for some strange reason, do not allow any iCloud backup to be password protected so it essentially means that should someone find software that can download all backups from an Apple ID and the respective iCloud account then they potentially have access to very personal or sensitive information.
This is what the hackers did
And this is what we will show you too (for educational purposes only)
The first thing you need is the PC software that was used which is called Elcomsoft Phone Password Breaker. This is from a Moscow based company and the software is sold on the basis that it allows you to recover files from phone backups from variety of different manufacturers (Apple, BlackBerry, and Microsoft) and is to be only used for legal purposes only.
However looking at their main menu for a start tells you that this software could definitely be used for all the wrong reasons.
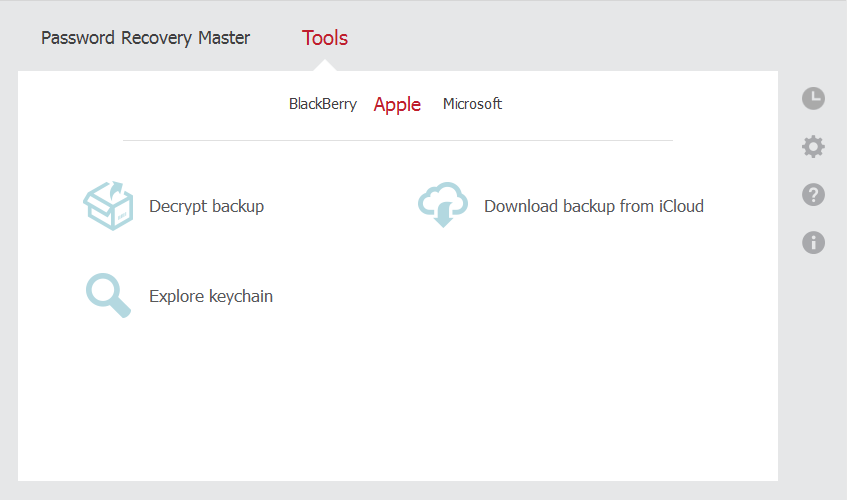
Explore keychain – The keychain is encrypted by Apple and contains all the passwords on the device (iPhone or iPad). Again, just drop an iTunes backup on to this option to view all passwords used on the phone across all installed applications that have been stored in the keychain.
For those who are interested the keychain stores the following information:
- Secure certificates
- Tokens (e.g. Twitter, Facebook etc.)
- Browser stored passwords
- Wi-Fi passwords for all networks a device was connected at least once
- Passwords, tokens and certificates stored by various applications
And the final option is what we are looking for – Download backup from iCloud.
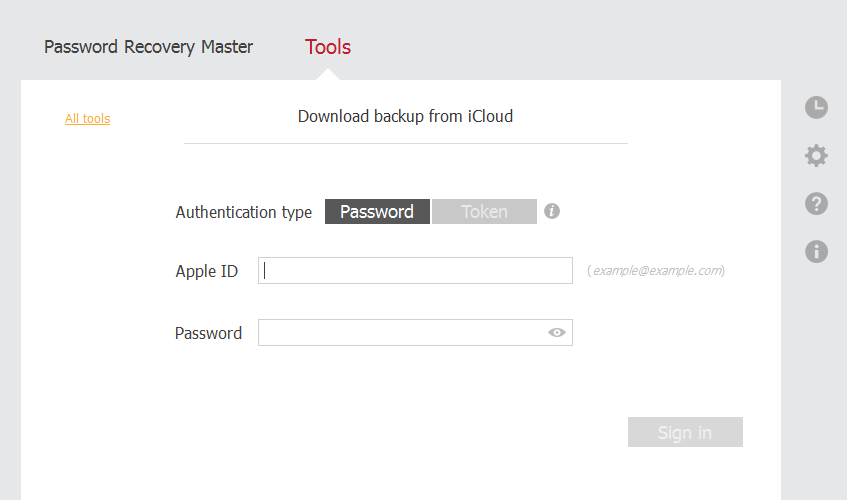
So we put in the username and password of our Apple ID that we set up for this exercise and then we sign in and our backup is clearly listed at the top.
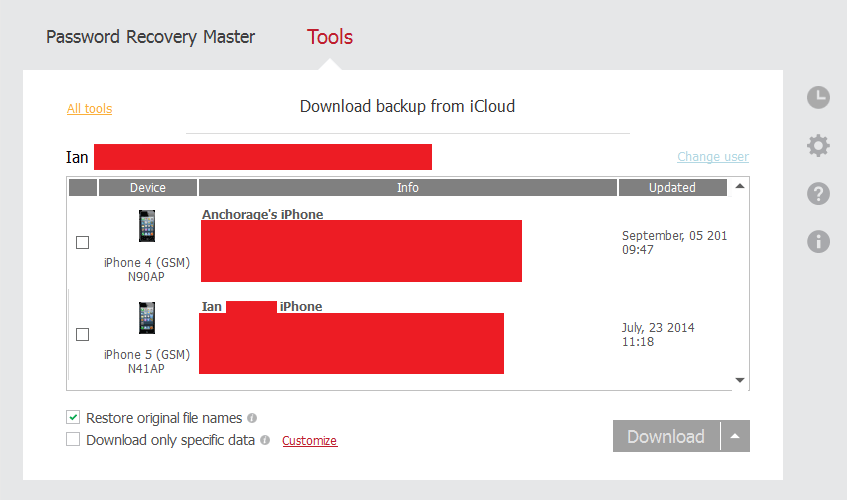
Essentially you just wait for the data to be downloaded to your PC and then you can pretty much do anything with it as you wish.
Apple makes this possible due to iCloud not having two step verification when you sign in (e.g. you sign in with a username and password and then answer a security question) which means that, as we have shown, just get the email address and password of an Apple ID and you potentially have access to phone backups which contains clearly sensitive and personal information.
How Can You Stop This From Happening?
The easiest way to stop yourself and your iDevice from becoming the next victim is simple.
- Make sure your Apple ID password is strong
- Turn off iCloud backups on the iDevice itself
- Use a cloud system with better backup and security such as Dropbox
Apple have since patched the brute force method used but they have still not improved iCloud security to encompass two step verification although, in the wake of this scandal, we hardly think Apple will rest and leave their premier cloud backup solution with such a gaping hole in it for the whole world to look in.
We hope that you have found this article useful. Don’t forget that you can actually use FlexiSPY on your own iPhone or iPad to act as a secure and effective device backup tool so, if this interests you, why not check out a 24 hour demo of FlexiSPY right now?
