Apples new 2FA renders iCloud spy apps useless
Key Points
- Apple now requires all iCloud accounts to have 2FA enabled.
- 2FA renders iCloud spy apps useless
- There is no way to turn off 2FA without creating a new Apple ID
- If you manage to create a new Apple ID without 2FA enabled, Apple gives you 2 weeks before automatically enabling 2FA
- During the time that 2FA is not enabled, when Apple detects that an iCloud spy app is accessing the iCloud backup, a password reset will be triggered and the Apple ID must use a new password. Doing this also breaks the iCloud solution
- iCloud spy apps only offer 6-8 features compared to FlexiSPY Jailbreak’s 50+
- iCloud spy apps are backed by Refund Policies which are biased against the Customer
- Low value for money considering reliability and limited features
Some competitors are marketing an iCloud spy app solution which they refer to as a “No-Jailbreak” solution – a title designed to mislead.
The reason for the subterfuge is that all true iPhone spy app applications require to be installed on the iPhone itself, which requires the device to be jailbroken. By referring to the solution as a No-Jailbreak solution and deliberately avoiding the mention of iCloud, they are misleading you into comparing apples to oranges.
The fact remains that if you wish to spy on an iPhone, FlexiSPY is the world’s only way to spy on an iPhone
How to Spy on an iPhone
There are two ways to retrieve data that the iPhone generates.
The first way is to use an application that captures all data and voice calls as they’re being generated.
This method requires an application.
The other method is to look at the historical data that has been backed up previously and extract the information from there. This method requires you to retrieve backup files from Apples iCloud service.
The Application Method
The Application Method is the one FlexiSPY invented in 2006 and requires configuring the device to support third-party applications by performing what is a called a Jailbreak. This Jailbreak process requires plugging the phone into a computer, opening the phones lock screen if it has a passcode, running a computer program and then installing FlexiSPY.
All information is then sent in real-time to a secure website where you can view it via browser or our FlexiVIEW mobile app.
The iCloud Method
The iCloud Method, or what is deceptively called “No-Jailbreak Solution”, depends on programmatically accessing Apples iCloud service where the iPhones backups are held.
It requires that Backups be configured and actually exist, and that the information that is useful to you is actually contained in the backup file.
Programmatic ace to the iCloud account is continually monitored by Apple and any suspicious activity is flagged and results in a number of problems. In the light of data breaches such as Jennifer Lawrence, Amber Heard, Hope Solo, it is understandable that Apple would do this.
Difference in features between both methods
Despite similar pricing, the iCloud Method offers only a handful of basic features, limited to what can actually be backed up from the phone.
On the other hand, FlexiSPYs application method offers close to 50 features, many of which no other competitor has including features such as Regular and IM Call Recording, Spy Call, RemCam, and RemVid, Ambient Recording, and more.
Below is a direct comparison of features offered between both solutions
iCloud
- Contacts
- Call Logs
- Text Messages
- iMessage
- Browser History
- Photos
- Videos
- GPS Location
iPhone Jailbreak
- Contacts
- Call Logs
- IM Call Logs
- Text Messages
- iMessage
- Browser History
- Keylogger
- Photos
- Videos
- Audio Files
- GPS Location
- Geo-fencing
- Phone Call Recording
- Call Intercept
- IM Call Recording
- Ambient Recording
- Spy call
- REM CAM
- REM VID
- Spoof SMS
- Emails
- Screenshots
- Network Connections
- Applications
- Keylogger
- SMS Remote Commands
- Dashboard Alerts
- Visibility Option
- Installation Service
- Hide Jailbreak
- & much more
Why Apples Latest 2FA Security Update Breaks the iCloud (“No-Jailbreak”) Solution
Due to a recent security patch implemented by Apple, no-Jailbreak (iCloud) solutions no longer function properly. Lets take a closer look at this.
In the past, No-Jailbreak solutions were able to have some functionality if, and only if, 2FA was disabled on the iCloud account. However recently, Apple mandated that all iCloud accounts now have 2FA enabled by default. This setting CANNOT be turned off. The only way to bypass this is to create a brand-new Apple ID from scratch and jump through complicated loopholes to choose to not enable 2FA.
Even if you succeed in this, Apple will routinely pressure the phone’s user to turn 2FA on, by sending them regular warnings that 2FA is disabled. All the user must do is accept the prompt, and the spy app will be broken.
Moreover, during any spaces of time in-between Apple prompting the user to turn on 2FA, when the no-Jailbreak solution connects to iCloud to retrieve the data, a password reset protocol may be triggered due to suspicious activity caused by the data retrieval. Once the iCloud password has been changed, this once again breaks the spy app.
But if you don’t believe our word, or the words of countless others who have been duped by no-Jailbreak solutions, here is one competitor admitting to our case above.
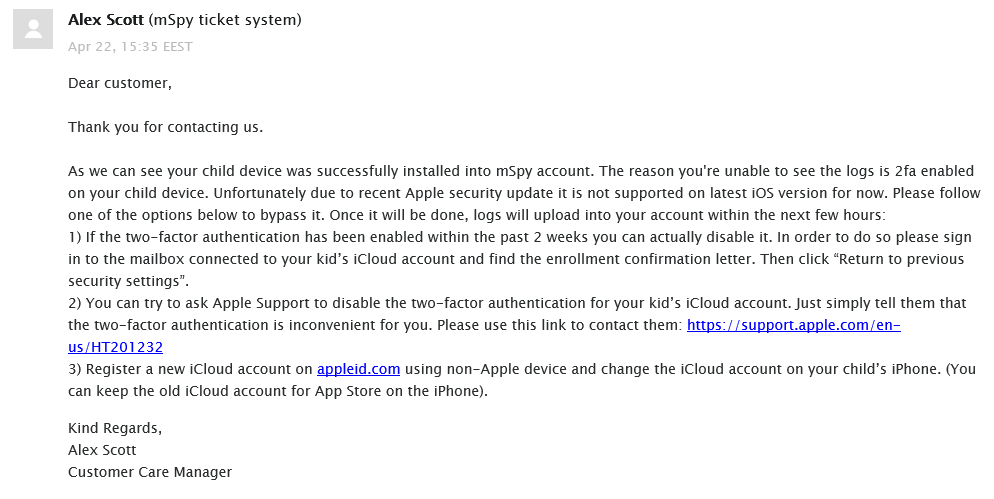
Testing mSpys iCloud Solution (“No-Jailbreak”): Our Findings
The first test. We first tried testing mSpy on a Non-Jailbroken iPhone 11, which had 2FA enabled by default. In order to set up mSpy, we needed the phone in our hand, the phones passcode to unlock the lock screen, the iCloud username, and the iCloud password. As part of the installation process, Apple generated a 2FA code and sent it to the iPhone, which we plugged in to our mSpy account. We then plugged in the phone to a power source, Wi-Fi, and locked the screen, as instructed by mSpy, and waited for the iCloud backup to occur.
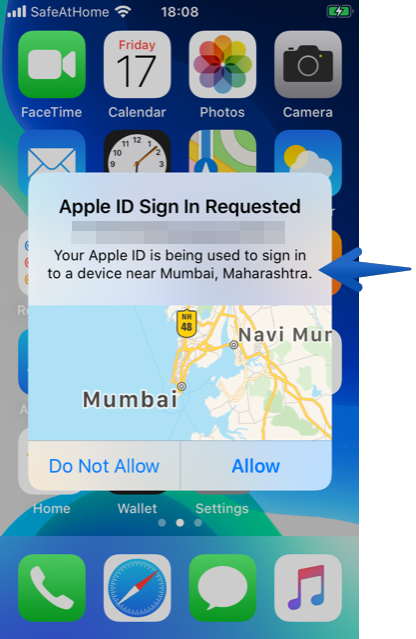
A week later, there was still no data inside our mSpy dashboard. After contacting support, they informed us that we would be unable to use mSpy as the phone had 2FA enabled.

The second test – new phone, new Apple ID. During the second test, we were able to set up a new Apple ID for our iPhone SE and went through the steps to leave 2FA disabled. Note that Apple policy stipulates that within the first two weeks of being created, the owner of the new iCloud account will still have the choice activate or deactivate 2FA.
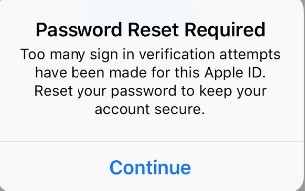
After installation however, we were locked out of the Apple account due to suspicious activity caused by mSpy accessing the iCloud backup. We then had to get the phone in our hand again, and reset the password via security questions and an email.
Throughout this testing we repeatedly received the following message which when tapped, broke mSpy.
The Bottom Line
As a result of this, one may be tempted to ask “is mSpy’s No-Jailbreak iCloud solution a scam?”
The answer to this question depends to what you call as a scam. If you define scam as telling an outright lie, then mSpy’s No-Jailbreak iCloud solution is probably not a scam.
However, if your definition of a scam is to subtlety mislead someone into believing that the iCloud solution is somehow equivalent to an iPhone Spy App, by omitting key pieces of information, then the answer to the scam question is pretty clear.